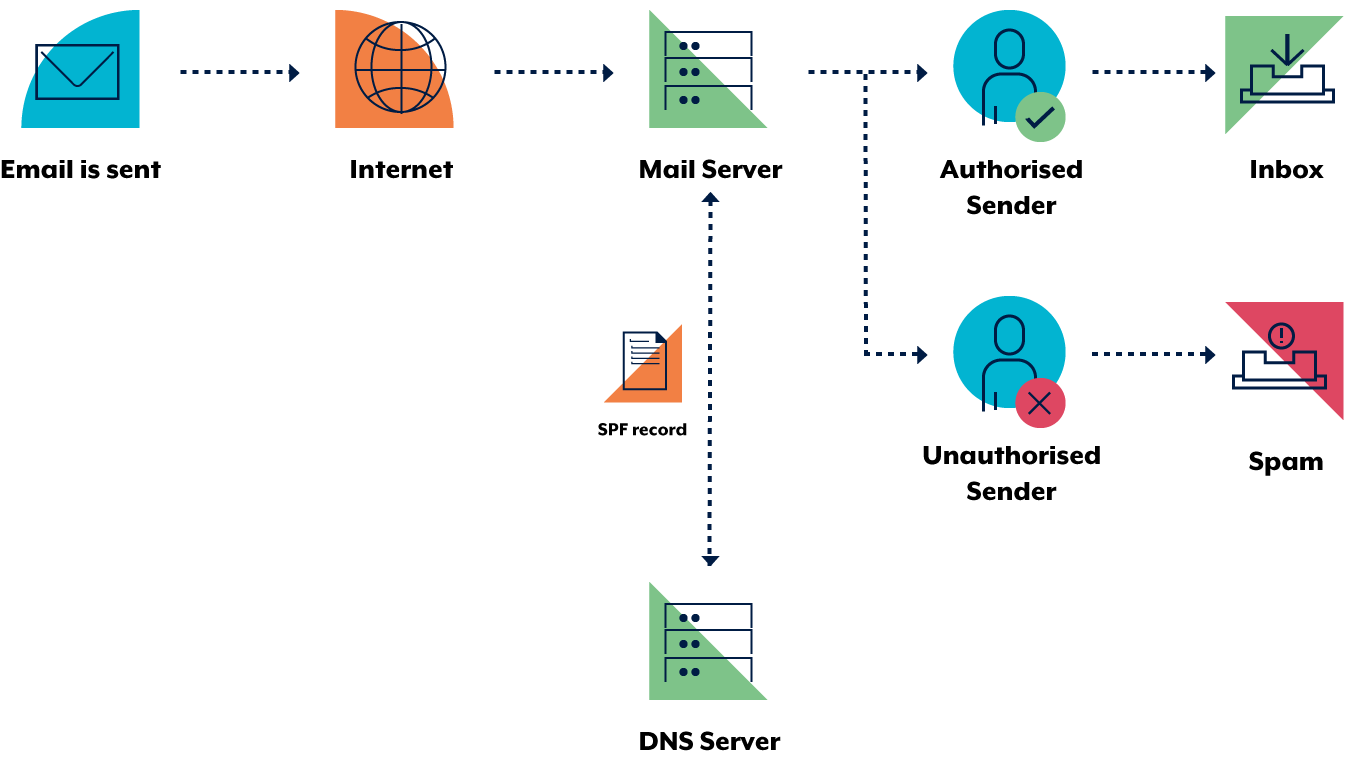
Sender Policy Framework (SPF):
The SPF is a protocol that ensures that an email is sent from a certain address. Internet Service Providers can use it to confirm that the mail server is authorized to send the message. An SPF record contains a list of the addresses that are allowed to send the email.Sender Policy Framework (SPF) Working:
SPF is a feature that allows you to send email to all the addresses that are allowed to do so by the domain. The record in the DNS contains all the details about the IP addresses that are permitted to send email. The SPF mechanism uses the return-path address of an email to identify the record of the sender’s SPF. When an email is delivered to a receiving server, it checks if the sender is on the list of approved senders. If so, a link is established between the email and the email domain, and the server continues to process the email as usual. Although an email might be real, its list of allowed senders might not be accurate. Also, the email might have been forwarded, which means that it could have come from anywhere. Unfortunately, there are many possible outcomes that can affect the link that an SPF can provide. DKIM is a new way to try and link an email back to a domain.Sender Policy Framework (SPF) Importance:
SPF is a vital component of ensuring that the sending infrastructure can deliver email on behalf of your domain. It can help verify that the infrastructure can handle the incoming email.- Increases domain reputation and email deliverability.
- Fights domain impersonation and email spoofing to protect your brand reputation.
- One of the foundational methods of email authentication for DMARC.
